- Home /
- Pixsysportal_security
PixsysPortal Security
Why PixsysPortal is safe
Architecture of components
In order to better understand the functioning and safety principles used, it is important to understand what components are present in the system and how they interact with each other.
| Pixsys Portal Server | The core of the infrastructure, where the database and services required for the management and initialisation of devices and connections reside |
| Pixsys Portal Runtime | Software running on remote devices to allow remote access. Available for various operating systems (Windows x64, Linux x64, Linux arm) |
| Pixsys Portal Client | Interactive web application allowing users to access their account and connect to remote devices |
Pixsys Portal Server security
All user and device information resides in a secure database with local access only.
Data exchange between the database and Pixsys Portal Runtime and Pixsys Portal Client products takes place by querying the RESTful API Server via secure requests (PixsysTPS, WSS, ...).
Pixsys Portal Server implements all the highest standards and requirements of the main Cyber security guidelines, so much so that it has been awarded an A+ rating on SSL Server Test (Powered by Qualys SSL Labs) portal.
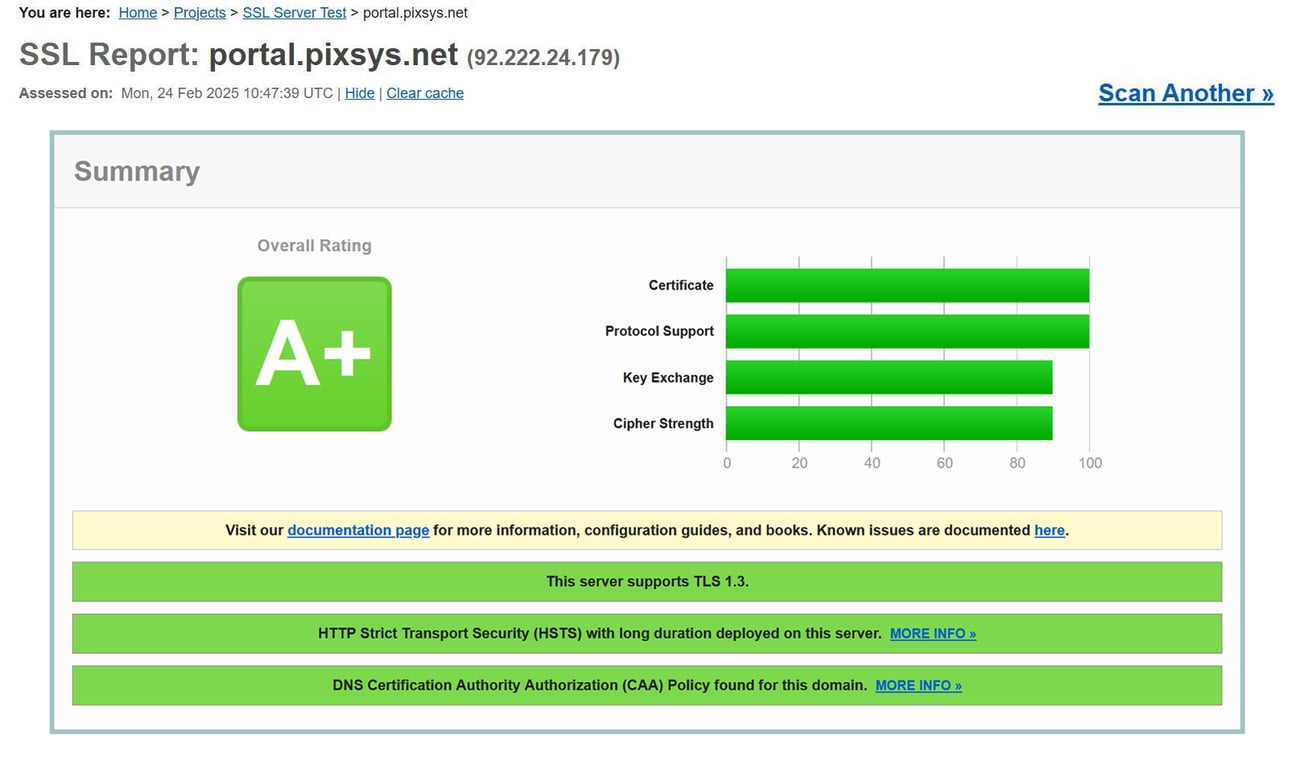
Protocols security
Pixsys Portal Server uses a server SSL certificate signed using SHA-256 with RSA by a recognised certification provider.
Only the following configuration combinations are allowed, ensuring that data in transit is encrypted and safe from interceptions, while offering optimal performance.
| TLS protocol | Cipher | Key exchange | Authentication | Encoding | Message Authentication Code (MAC) |
|---|---|---|---|---|---|
| TLS 1.2 / TLS 1.3 | ECDHE-ECDSA-AES256-GCM-SHA384 | ECDHE (Elliptic Curve Diffie-Hellman Ephemeral) | ECDSA (Elliptic Curve Digital Signature Algorithm) | AES256-GCM (Advanced Encryption Standard in Galois/Counter Mode) | SHA384 (Secure Hash Algorithm 384-bit) |
| TLS 1.2 / TLS 1.3 | ECDHE-RSA-AES256-GCM-SHA384 | ECDHE (Elliptic Curve Diffie-Hellman Ephemeral) | RSA (Rivest-Shamir-Adleman) | AES256-GCM (Advanced Encryption Standard in Galois/Counter Mode) | SHA384 (Secure Hash Algorithm 384-bit) |
| TLS 1.2 / TLS 1.3 | ECDHE-ECDSA-CHACHA20-POLY1305 | ECDHE (Elliptic Curve Diffie-Hellman Ephemeral) | ECDSA (Elliptic Curve Digital Signature Algorithm) | CHACHA20 (Stream Cipher) | POLY1305 (Message Authentication Code) |
| TLS 1.2 / TLS 1.3 | ECDHE-RSA-CHACHA20-POLY1305 | ECDHE (Elliptic Curve Diffie-Hellman Ephemeral) | RSA (Rivest-Shamir-Adleman) | CHACHA20 (Stream Cipher) | POLY1305 (Message Authentication Code) |
| TLS 1.2 / TLS 1.3 | ECDHE-ECDSA-AES128-GCM-SHA256 | ECDHE (Elliptic Curve Diffie-Hellman Ephemeral) | ECDSA (Elliptic Curve Digital Signature Algorithm) | AES128-GCM (Advanced Encryption Standard in Galois/Counter Mode) | SHA256 (Secure Hash Algorithm 256-bit) |
| TLS 1.2 / TLS 1.3 | ECDHE-RSA-AES128-GCM-SHA256 | ECDHE (Elliptic Curve Diffie-Hellman Ephemeral) | RSA (Rivest-Shamir-Adleman) | AES128-GCM (Advanced Encryption Standard in Galois/Counter Mode) | SHA256 (Secure Hash Algorithm 256-bit) |
The cookies used are configured with the attributes Secure and HttpOnly, ensuring that they are only transmitted over secure connections and are not accessible via JavaScript.
Access security
A crucial element of security is the protection of user credentials. Passwords are encrypted with the Bcrypt algorithm, which adds an extra layer of security against brute force attacks.
To ensure secure passwords, Pixsys Portal imposes even higher complexity requirements than the IEC 62443 standard:
- minimum length of 12 characters
- at least 1 lower case alphabetical character
- at least 1 capital alphabetical character
- at least 1 special character
- at least 1 numeric character
Once authenticated, the user via Pixsys Portal Client or the device via Pixsys Portal Runtime inherently obtains a signed JSON Web Tokens (JWT), containing information such as role and expiry date, which is verified with each request. In the case of Pixsys Portal Client the token is saved on cookies with the above-mentioned characteristics, making it impossible the steal and consequently impersonation attacks.
To avoid brute force authentication attacks, customised rules were installed on the Web Application Filter (WAF) to block after a few failed login attempts, all requests originating from the same public IP for a few minutes.
Pixsys Portal implements a Role-Based Access Control (RBAC) system to ensure that each user only accesses permitted resources.
Pixsys Portal Runtime security
The first time Pixsys Portal Runtime connects online, a unique UID and password are generated and saved locally on the device.
The generated UID is linked to the hardware infrastructure of the device.
Subsequently, before any request to Pixsys Portal Server, the device must authenticate itself to verify its authenticity.
Connections security
Both VPN and direct control (WebRTC) connections are Peer-to-Peer communications: during the connection phase, the two communicators (Pixsys Portal Client and Pixsys Portal Runtime) talk to Pixsys Portal Server for the sole purpose of exchanging the information needed for the connection, after which they connect directly to each other, without the need for additional firewall configurations.
In the case of a VPN connection, participants in the connection will communicate with the VPN Signaling Server, in the case of a WebRTC (Web Real-Time Communication) connection, participants will communicate with the WebRTC Signaling Server.
End-to-end encryption is used to protect the content of communications, through AES encryption.
Additional security measures implemented
Protection against XSS Attacks
- Input sanitisation: Every user input is validated and sanitised on both client and server side.
- Security Header: Implementation of Content-Security-Policy (CSP) headers to limit the execution of unauthorised scripts.
- Secure Template Engines: Using frameworks that automatically prevent XSS.
Protection against CSRF Attacks
- Token CSRF: Each request with status uses a unique CSRF token verified by the server.
- Cookie configuration: Cookies use the Secure, HttpOnly and Domain directives to prevent sending to external domains, and only with secure connections.
Protection against SQL Injection
- Parametrics Query: Exclusive use of parameterised queries or prepared statements.
- ORM Sicuri: Utilizzo di ORM (Object-Relational Mapping) che gestiscono l'escaping automatico dei dati.
- Validazione Input: Convalida e sanitizzazione di tutti i dati ricevuti dagli utenti.
Protection against Clickjacking
- Header X-Frame-Options: Configuration of the header with SAMEORIGIN to prevent inclusion of the site in external frames.
- Content Security Policy (CSP): Use of CSP to prevent clickjacking attacks.
Protection against DOS/DDoS attacks
- Rate Limiting: Limitation of requests per IP and/or user.
- WAF: Configuring a WAF (Web Application Firewall) to identify and block suspicious traffic.
Vulnerability Disclosure management
- Regular Updates: Application of security patches and updates.
- Penetration Testing: Periodic testing for unknown vulnerabilities.
- SAST and SCA: Static code analysis and checking of third-party packages periodically and with each change during development
- Bug Bounty Program: Invitation to security researchers to report vulnerabilities in exchange for rewards.
Conclusion
Thanks to the implementation of the measures listed above, the Pixsys Portal infrastructure is protected against major vulnerabilities and complies with modern security requirements. Possible improvements will be made based on the feedback received and the evolution of threats.